
- September 23, 2025
- Tejhaksh
- 0 Comments
- Cyberattack, Uncategorized
What is a Cyberattack? Types of Cyberattacks and Effective Protection Tips
In today’s world, with our lives, work, and businesses so reliant on the internet, cyber attacks have become a major threat. Whether it’s a small business, a large corporation, or an individual, cybercriminals can target anyone. These attacks can steal our data, cause financial loss, lead to identity theft, and damage our reputation. So, what exactly are cyber attacks, what causes them, who do criminals target, and how can we protect ourselves? This guide will explore the different types of cyber attacks, their causes, and simple yet effective ways to defend against them.
What is a cyber attacks?
A cyber attack is a deliberate attack carried out by hackers, cybercriminals, or hostile organizations. Its purpose is to damage, disrupt, or gain unauthorized control over computers, mobile devices, networks, or other digital devices. These attacks exploit technical vulnerabilities, software weaknesses, or human errors.
Main Objectives of Cyber Attacks
Cyber attackers can have several motives. Some of the primary reasons are as follows:
- Data Theft – Hackers attempt to steal sensitive information such as financial records, credit card details, passwords, or trade secrets. This information can later be sold or used for other malicious purposes.
- Disruption of Operations – Sometimes, the aim of a cyber attack is to shut down a system, website, or server, thus disrupting normal operations. To prevent this, companies and organizations need to implement robust security measures.
- Financial Gain – Many attackers conduct cyber attacks to make money. For example, in ransomware attacks, they lock your data and demand a ransom for its release. Online fraud and unauthorized financial transactions are also common.
- Espionage – Cyber criminals sometimes aim to obtain confidential information for political, military, or business gain. This information can be used to harm competitors or adversary agencies.
- Reputation Damage – A cyber attack can also be aimed at damaging the reputation of a company or individual. This undermines their credibility and erodes public trust.
In simple terms, a cyber attack is a form of digital theft or sabotage. Attackers exploit vulnerabilities in your systems or devices. Unlike traditional crimes, cyber attacks can be launched from anywhere in the world, often anonymously, and have the potential to cause immense damage.
Today, with the increasing use of cloud computing, artificial intelligence, and Internet of Things (IoT) devices, the number and complexity of cyber threats are constantly growing. Cyber attacks are no longer limited to large corporations or government agencies. Ordinary individuals, small businesses, and even personal smartphones are now targets. Therefore, it is crucial for everyone and every organization to take cybersecurity seriously.
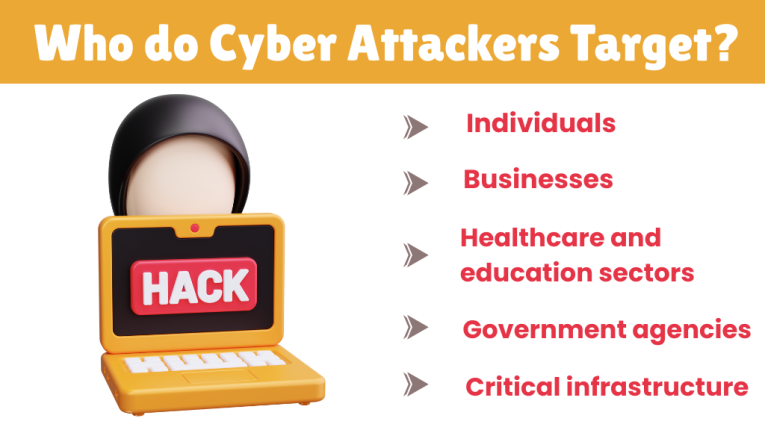
Who do cyber attackers target?
Cyber attackers can target anyone. They can attack any individual, organization, or institution if they can gain access to data or other benefits. Some common targets include:
- Individuals – To steal personal information, social media accounts, banking details, or passwords.
- Businesses – Especially small and medium-sized businesses with weak cybersecurity.
- Government agencies – For political, financial, or strategic advantage.
- Healthcare and education sectors – These sectors store a great deal of sensitive personal and institutional data.
- Critical infrastructure – Such as power grids, transportation systems, and defense networks.
In fact, any person or organization connected to the internet can be a target of a cyber attack. Therefore, it is crucial for everyone to prioritize their digital security.
What Causes Cyber Attacks?
Cyber attacks don’t happen out of the blue. They occur when attackers exploit vulnerabilities in a system or network. These vulnerabilities can be in technology, processes, or human behavior. Here are some of the most common causes of cyber attacks:
Weak Passwords and Poor Security Practices
Easy or reused passwords provide hackers with easy access to any account. Without multi-factor authentication (MFA), even a single leaked password can compromise an entire system.
Outdated or Unpatched Software
If operating systems or applications aren’t updated, hackers can exploit vulnerabilities. Systems with outdated software are easily identifiable and vulnerable to attacks.
Human Error
Many cyber attacks result from human mistakes. For example, clicking on phishing links, downloading suspicious attachments, using unsecured Wi-Fi, or accidentally sharing sensitive information. Even the most secure systems can be compromised by employee or user negligence.
Lack of Cybersecurity Awareness
Many organizations fail to train their employees on proper cybersecurity practices. This makes it easier for hackers to conduct social engineering attacks, where they trick people into revealing confidential information or granting access.
Financial Gain
Most cyber attacks are motivated by financial gain. Attackers can hold data for ransom, steal personal and financial data for fraud, or sell it on the dark web.
Political or Ideological Reasons
Some cyber attacks are carried out by hacktivist groups or state-sponsored attackers. Their motives may include espionage, spreading propaganda, damaging government or national infrastructure, or engaging in cyber warfare.
Insecure Networks and Devices
With the rapid growth of the Internet of Things (IoT), many smart devices (such as cameras, routers, and wearables) are inherently less secure. Hackers use these as entry points for larger cyber attacks.
Internal threats
Not all cyber attacks originate from external sources. Sometimes, disgruntled employees, contractors, or business partners can misuse their access to steal or leak sensitive data.
12 Most Common Types of Cyber Attacks
Cyber threats are constantly evolving and increasing. Hackers never stop finding new methods to exploit security gaps. Yet, certain types of cyber attacks occur more frequently across the globe. Here’s a simple explanation of some of the most prevalent ones:
1. Malware
Malware is a type of malicious software designed to damage a system or gain unauthorized access to it. The main categories include viruses, worms, Trojans, ransomware, and spyware. Malware often spreads through malicious email attachments, risky websites, or pirated software downloads. After infiltrating a system, malware can steal personal information, slow down performance, lock important files, and in some cases, give hackers remote access to your device.
2. Denial-of-Service (DoS) Attack
In a DoS attack, cyber criminals overwhelm a server, system, or network by sending an excessive amount of traffic. This overwhelms the system, making it unavailable to legitimate users. A more sophisticated and dangerous version of this is the Distributed Denial-of-Service (DDoS) attack. In this type of attack, hackers use a network of compromised devices (a botnet) to launch a large-scale attack simultaneously. Such attacks can cause significant financial and operational losses for businesses.
3. Phishing
Phishing is a type of fraud in which hackers create fake emails, text messages, or websites. These messages or websites appear to be from a legitimate bank or company. The goal is to trick users into revealing sensitive information such as login details, passwords, or credit card information. Sometimes, phishing is also used to distribute malware. It is one of the most common and effective methods of cyber attack.
4. Spoofing
In a spoofing attack, a hacker impersonates a trusted entity or individual to mislead users or systems. This can be done in several ways:
- Email spoofing – Faking a legitimate email address.
- Website spoofing – Creating a fake website that looks genuine.
- IP spoofing – Faking a legitimate IP address.
The main objective of spoofing is to steal sensitive information or spread malware.
5. Identity-Based Attacks
In these attacks, hackers exploit the identity of legitimate users to gain access to systems using stolen or forged credentials. They might use leaked passwords, brute-force attacks, or credential stuffing. This can lead to identity theft, data breaches, or fraudulent transactions.
6. Code Injection Attacks
Code injection occurs when hackers exploit vulnerabilities in a website or software to inject malicious code. Common examples include:
- SQL injection – Injecting malicious SQL commands into a database to steal or alter data.
- Cross-Site Scripting (XSS) – Injecting malicious scripts into a user’s web page.
These attacks can result in data theft, system compromise, and sometimes even complete website takeover.
7. Supply Chain Attacks
In a supply chain attack, hackers don’t directly target a business. Instead, they target vulnerabilities in its supply chain, such as third-party vendors, contractors, or software providers. Once they compromise one link in the chain, hackers can gain access to the larger organization. A well-known example is the SolarWinds attack, where malware was inserted into a software update, affecting thousands of organizations worldwide.
8. Social Engineering Attacks
Social engineering attacks don’t exploit technical vulnerabilities; they focus on manipulating human behavior. Attackers trick people into revealing sensitive information or granting access to systems. This can be done through fake phone calls, impersonating tech support, pretexting, or other deceptive tactics. Because it leverages trust, social engineering is difficult to defend against.
9. Insider Threats
Not all cyberattacks originate from external sources. Sometimes, employees, contractors, or trusted individuals misuse their access. This can be intentional, such as stealing data out of spite, or unintentional, such as carelessly leaking sensitive information. Insider attacks are dangerous because the insider already has legitimate access to the system.
10. DNS Tunneling
DNS tunneling is a sophisticated attack where hackers use the Domain Name System (DNS) to covertly transmit data or communicate with compromised systems. Since DNS is considered a trusted protocol, this malicious traffic is difficult to detect. Hackers can bypass firewalls and steal sensitive data using this method.
11. IoT-Based Attacks
With the rise of the Internet of Things (IoT), smart cameras, thermostats, fitness trackers, and connected home devices have become commonplace in our daily lives. While these devices offer convenience, they often have weak security measures, such as default passwords, unencrypted data transfer, or outdated firmware. Hackers exploit these vulnerabilities to gain unauthorized access to these devices. They can then steal sensitive data, disrupt operations, or use these devices to launch attacks like DDoS on larger networks.
12. AI-Enabled Attacks
Today, cybercriminals are using artificial intelligence (AI) to conduct faster and more sophisticated attacks. AI-enabled attacks utilize machine learning algorithms to create automated, personalized, and difficult-to-detect attacks. Examples include:
- Automated Phishing – AI generates highly convincing and personalized phishing emails based on user behavior.
- Deepfakes – Creating fake videos or audio to impersonate individuals, commit fraud, or manipulate public opinion.
- Smart Malware – Malware that evades traditional antivirus programs by dynamically changing its behavior.
With AI, attackers can make their attacks more effective, target vulnerabilities more easily, and circumvent standard security measures. Therefore, AI-enabled attacks are among the most dangerous cyber threats in today’s digital age.
How to Protect Yourself from Cyber Attacks
The good news is that you can significantly protect yourself and your organization from cyber attacks by following some simple and effective security measures.
Easy Ways to Prevent Cyber Attacks:
- Create Strong Passwords – Use complex and unique passwords for your accounts and change them regularly.
- Enable Multi-Factor Authentication (MFA) – This adds an extra layer of security and makes it harder for hackers to access your accounts.
- Keep Your Software Updated – Always keep your computer, mobile devices, and apps up to date with the latest versions and security patches.
- Install a Firewall and Antivirus – These tools help detect and block threats.
- Be Cautious of Phishing Emails – Don’t click on suspicious links or open attachments from unknown senders.
- Limit Access – Grant employees or users access only to the data they need.
- Encrypt Your Data – This makes it difficult to read even if the data is stolen.
- Back Up Your Data – Regularly back up your important data, especially to protect against ransomware attacks.
- Use Secure Wi-Fi – Use encrypted networks and strong passwords.
- Cybersecurity Awareness Training – Train your employees about cyber threats so they can recognize common cyber attacks and respond appropriately.
Final Thoughts
Cyber attacks are no longer a distant threat. They are a real danger that affects millions of people and businesses worldwide every day. Whether it’s a phishing email, malware, or an advanced AI-based attack, vigilance is the best defense.
By understanding what cyber attacks are, the different types, why they occur, and how to prevent them, you can protect your personal data, safeguard your business, and strengthen your overall cybersecurity posture.
Remember: prevention is always better than cure. Use strong passwords, keep your software and apps updated, and educate your employees about cybersecurity. These simple practices can save you from major data breaches and financial losses. Stay vigilant and stay safe.




Leave a Comment